Configuring Advanced Windows Server 2012 Services 온라인 연습
최종 업데이트 시간: 2025년06월22일
당신은 온라인 연습 문제를 통해 Microsoft 70-412 시험지식에 대해 자신이 어떻게 알고 있는지 파악한 후 시험 참가 신청 여부를 결정할 수 있다.
시험을 100% 합격하고 시험 준비 시간을 35% 절약하기를 바라며 70-412 덤프 (최신 실제 시험 문제)를 사용 선택하여 현재 최신 448개의 시험 문제와 답을 포함하십시오.
정답:
Explanation:
So what about changing the cache size? Well, you can't modify the cache size, but you can specify it at the time that you create a new virtual hard disk. In order to do so, you have to use Windows PowerShell.
New-VirtualDisk StoragePoolFriendlyName "<storage pool name>" FriendlyName "<v
Reference: Using Windows Server 2012's SSD Write-Back Cache
정답:
Explanation:
Proposed permissions enable an administrator to more accurately model the impact of potential changes to access control settings without actually changing them.
Reference: Access Control and Authorization Overview
http://technet.microsoft.com/en-us/library/jj134043.aspx
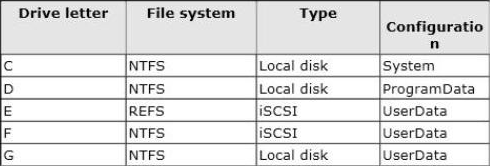
정답:
Explanation:
Volumes that are candidates for deduplication must conform to the following requirements:
* Must not be a system or boot volume. (not A)
* Can be partitioned as a master boot record (MBR) or a GUID Partition Table (GPT), and must be formatted using the NTFS file system. (not C)
* Can reside on shared storage, such as storage that uses a Fibre Channel or an SAS array, or when an iSCSI SAN and Windows Failover Clustering is fully supported.
* Do not rely on Cluster Shared Volumes (CSVs). You can access data if a deduplication-enabled volume is converted to a CSV, but you cannot continue to process files for deduplication.
* Do not rely on the Microsoft Resilient File System (ReFS).
* Must be exposed to the operating system as non-removable drives. Remotely-mapped drives are not supported.
Ref: Plan to Deploy Data Deduplication
http://technet.microsoft.com/en-us/library/hh831700.aspx
정답: 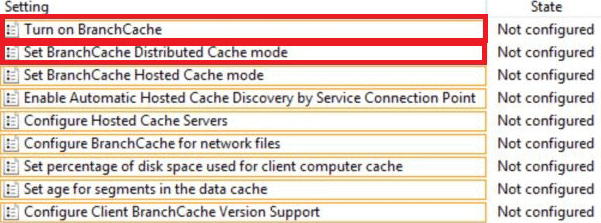
Explanation:
BranchCache is disabled by default on client computers.
Take the following steps to enable BranchCache on client computers:
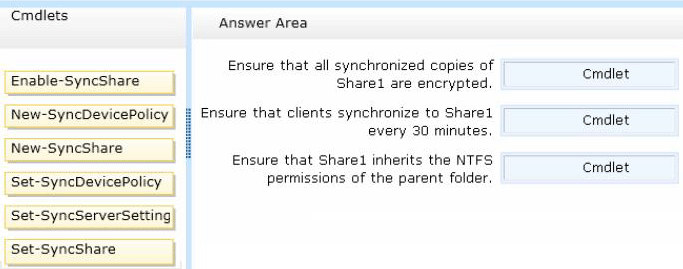
정답: 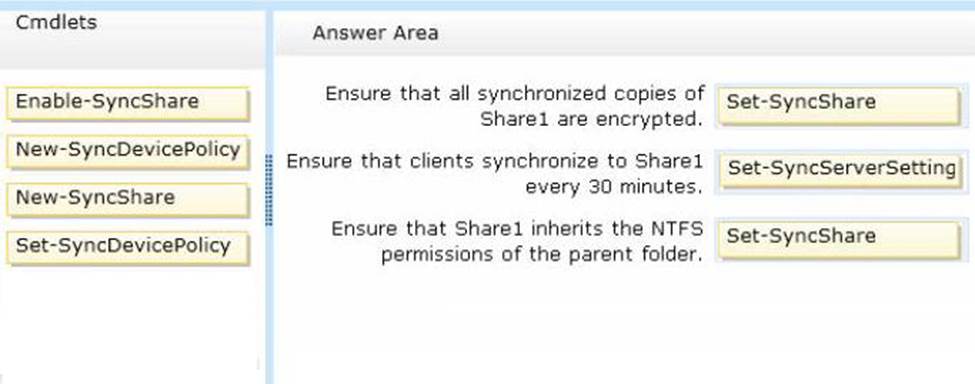
Explanation:
* (box 1) Set-SyncShare
The Set-SyncShare cmdlet modifies the settings for a sync share.
/ parameter: -RequireEncryption<Boolean>
Indicates whether the sync server requests that the contents of Work Folders be encrypted on each PC and device that accesses the sync share.
* (box 2) Set-SyncServerSettings
Parameter: -MinimumChangeDetectionMins<UInt32>
Specifies the time, in minutes, before the Sync Share server detects changes on devices and syncs the client and server.
* (box 3): Example: Modify a sync share to enable inherited permissions
This command modifies settings on the share named Share01, and sets KeepParentFolderPermission to enable the share to inherit permissions from the parent folder.
Windows PowerShell
PS C:\> Set-SyncShare Share01 -KeepParentFolderPermission
Reference: Set-SyncShare; Set-SyncServerSettings
정답:
Explanation:
Access-denied assistance can be configured by using the File Server Resource Manager console on the file server.
Note: Access-denied assistance is a new feature in Windows Server 2012, which provides the following ways to troubleshoot issues that are related to access to files and folders:
* Self-assistance. If a user can determine the issue and remediate the problem so that they can get the requested access, the impact to the business is low, and no special exceptions are needed in the central access policy. Access-denied assistance provides an access-denied message that file server administrators can customize with information specific to their organizations. For example, an administrator could set the message so that users can request access from a data owner without involving the file server administrator.
Reference: Scenario: Access-Denied Assistance
정답:
Explanation:
Windows Server 2012 includes an iSCSI Target role that, along with Failover Clustering, allows it to become a cost-effective and highly-available iSCSI Storage Array.
We can connect from our Hyper-V host to the iSCSI target on the storage array with the following PowerShell command line:
New-IscsiTargetPortal CTargetPortalAddress <IP_Address or FQDN of storage array>
$target = Get-IscsiTarget
Connect-IscsiTarget CNodeAddress $target.NodeAddress
Incorrect:
Not B. Discovery Domains in an iSCSI fabric, like zones in a Fibre Channel fabric, enable you to partition the storage resources in your storage area network (SAN). By creating and managing Discovery Domains, you can control the iSCSI targets that each iSCSI initiator can see and log on to.
Reference: Configure iSCSI Target Server Role on Windows Server 2012
정답: 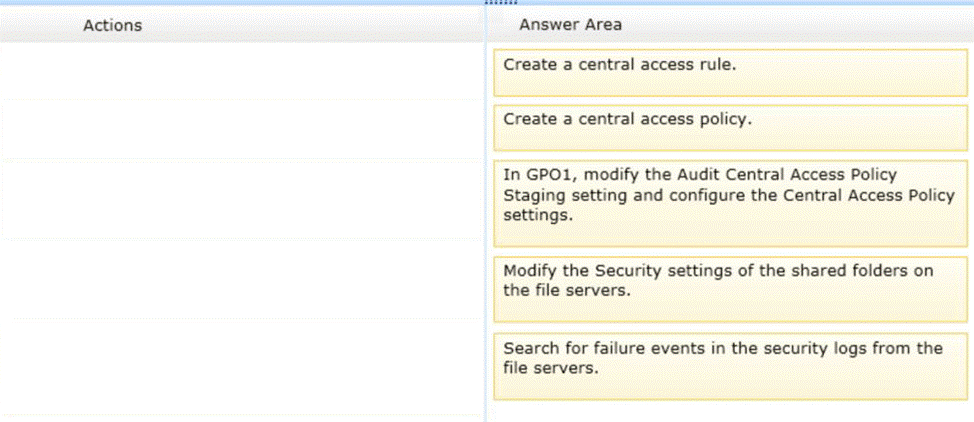
Explanation:
* Configure a central access rule
* Configure a central access policy (CAP) (with help of central access rules)
* Deploy the central access policy (through GPO)
* Modify security settings
* Check the result
Reference: Deploy a Central Access Policy (Demonstration Steps)
http://technet.microsoft.com/en-us/library/hh846167.aspx
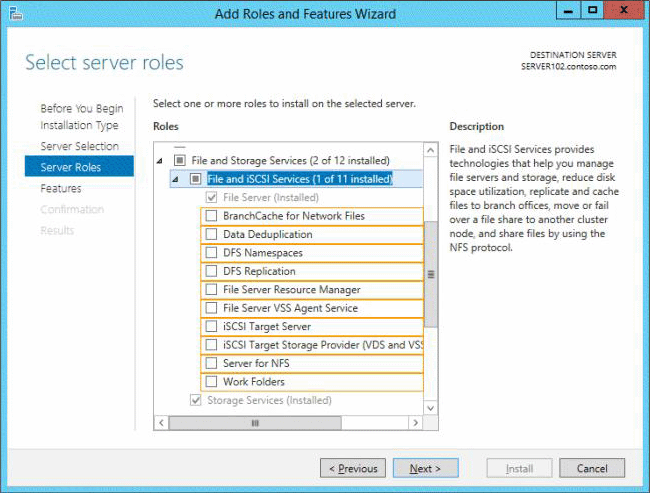
정답: 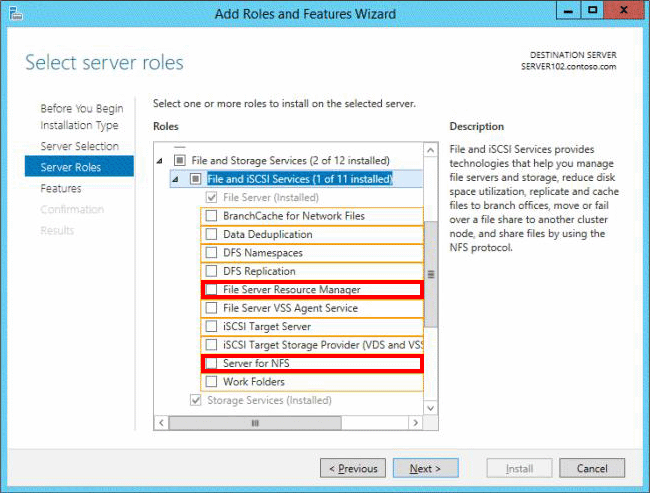
Explanation:
*File Server Resource Manager Role
File Server Resource Manager is a set of features that allow you to manage and classify data that is stored on file servers.
Note: NFS Share C Advanced
This advanced profile offers additional options to configure a NFS file share.
Set the folder owners for access-denied assistance
Configure default classification of data in the folder for management and access policies
Enable quotas
Reference: How to share a folder in Windows Server 2012.
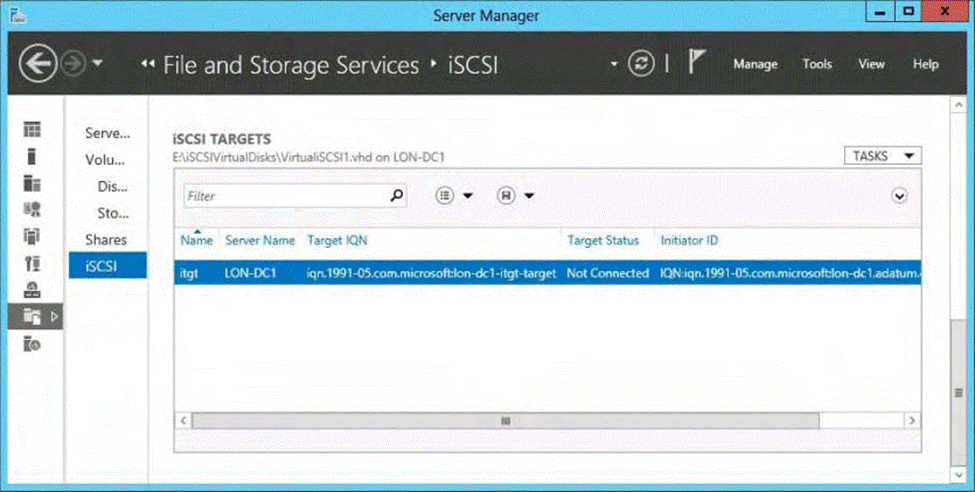
정답:
Explanation:
The virtual disk has the option to change the lun ID, no other option available in the answers appears to allow this change.
Note: Logical unit numbers (LUNs) created on an iSCSI disk storage subsystem are not directly assigned to a server. For iSCSI, LUNs are assigned to logical entities called targets.
정답: 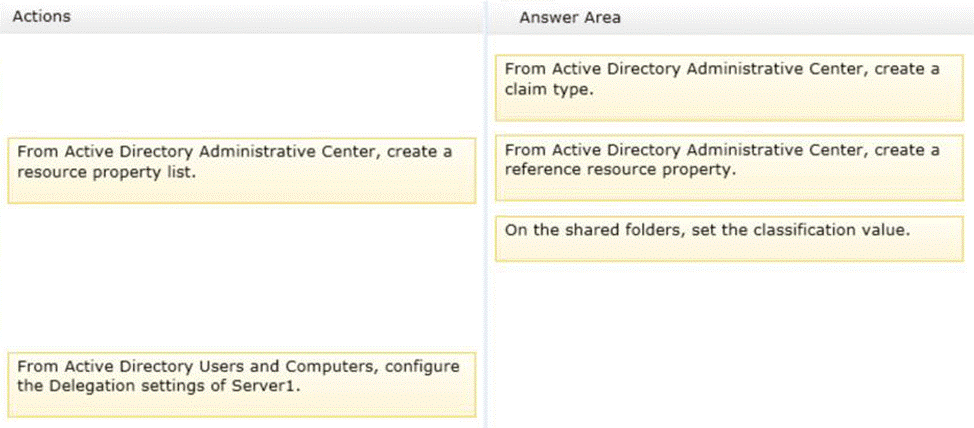
Explanation:
* First create a claim type for the property, then create a reference resource property that points back to the claim. Finally set the classification value on the folder.
* Configure the components and policy
정답:
Explanation:
Enables you to quickly set up a system partition, or to repair the boot environment located on the system partition. The system partition is set up by copying a simple set of Boot Configuration Data (BCD) files to an existing empty partition.
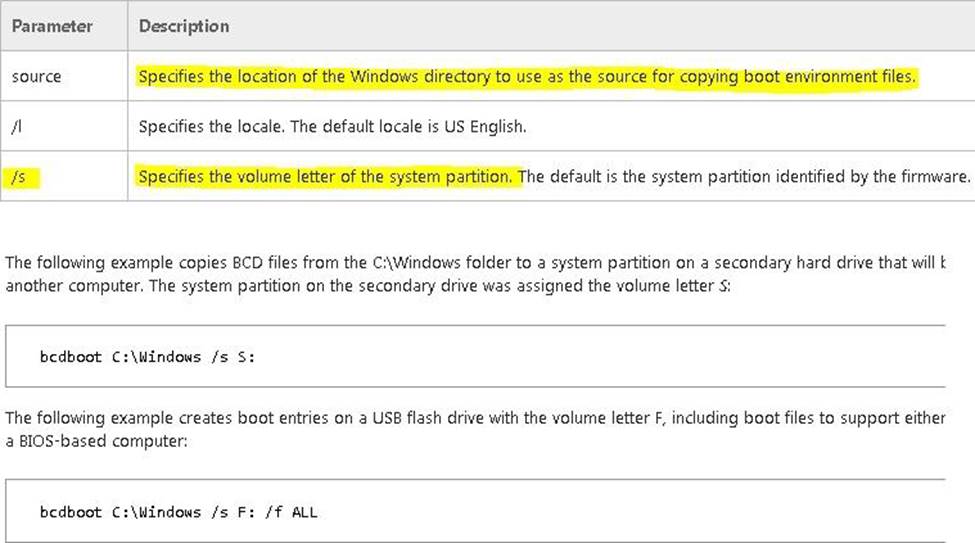
Reference: BCDboot Command-Line Options
정답:
Explanation:
You first have to enable replication on the Replica server―Server2--by going to the server and modifying the "Replication Configuration" settings under Hyper-V settings. You then go to VM1--which presides on Server1-- and run the "Enable Replication" wizard on VM1.
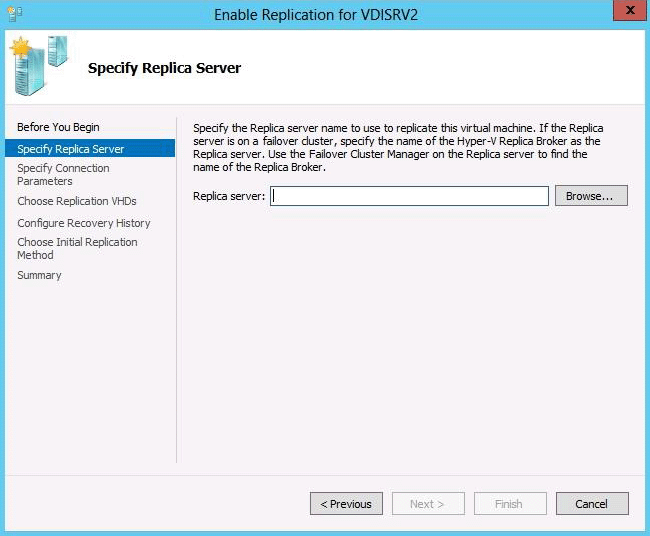
정답:
Explanation:
Extend Replication through UI:
Before you Extend Replication to third site, you need to establish the replication between a primary server and replica server.
Once that is done, go to replica site and from Hyper-V UI manager select the VM for which you want to extend the replication. Right click on VM and select “Replication->Extend Replication …”. This will open Extend Replication Wizard which is similar to Enable Replication Wizard.
NOTE: You configure a server to receive replication with Hyper-V Manager, in this situation the replica site is assumed to be the Replica Server. Therefore you extend replication from VM1 on Host2.
Note 2: With Hyper-V Extend Replication feature in Windows Server 2012 R2, customers can have multiple copies of data to protect them from different outage scenarios. For example, as a customer I might choose to keep my second DR site in the same campus or a few miles away while I want to keep my third copy of data across the continents to give added protection for my workloads. Hyper-V Replica Extend replication exactly addresses this problem by providing one more copy of workload at an extended site apart from replica site.
Reference: Hyper-V Replica: Extend Replication
http://blogs.technet.com/b/virtualization/archive/2013/12/10/hyper-v-replica-extend-replication.aspx
정답:
Explanation:
Performs a system recovery (bare metal recovery). This subcommand can be run only from the Windows Recovery Environment.
* -backupTarget
Specifies the storage location that contains the backup or backups that you want to recover. This parameter is useful when the storage location is different from where backups of this computer are usually stored.
References: Wbadmin start sysrecovery https://technet.microsoft.com/en-us/library/cc742118.aspx