GIAC Advanced Smartphone Forensics 온라인 연습
최종 업데이트 시간: 2025년10월15일
당신은 온라인 연습 문제를 통해 GIAC GASF 시험지식에 대해 자신이 어떻게 알고 있는지 파악한 후 시험 참가 신청 여부를 결정할 수 있다.
시험을 100% 합격하고 시험 준비 시간을 35% 절약하기를 바라며 GASF 덤프 (최신 실제 시험 문제)를 사용 선택하여 현재 최신 71개의 시험 문제와 답을 포함하십시오.
정답:
정답:
Explanation:
Reference: https://pdfs.semanticscholar.org/7f33/9156f47345bd102c9b05f45f9bfe4c182720.pdf
정답:
정답:
Explanation:
The Mobile Equipment ID (MEID), also found under the battery cover, is a 56 bit number which replaced the ESN due to the limited number of 32 bit ESN numbers. The MEID is listed in hex, where the first byte is a regional code, next three bytes are a manufacturer code, and remaining three bytes are a manufacturer-assigned serial number. Reference: https://sites.google.com/site/bbayles/index/cdma_hardware_id
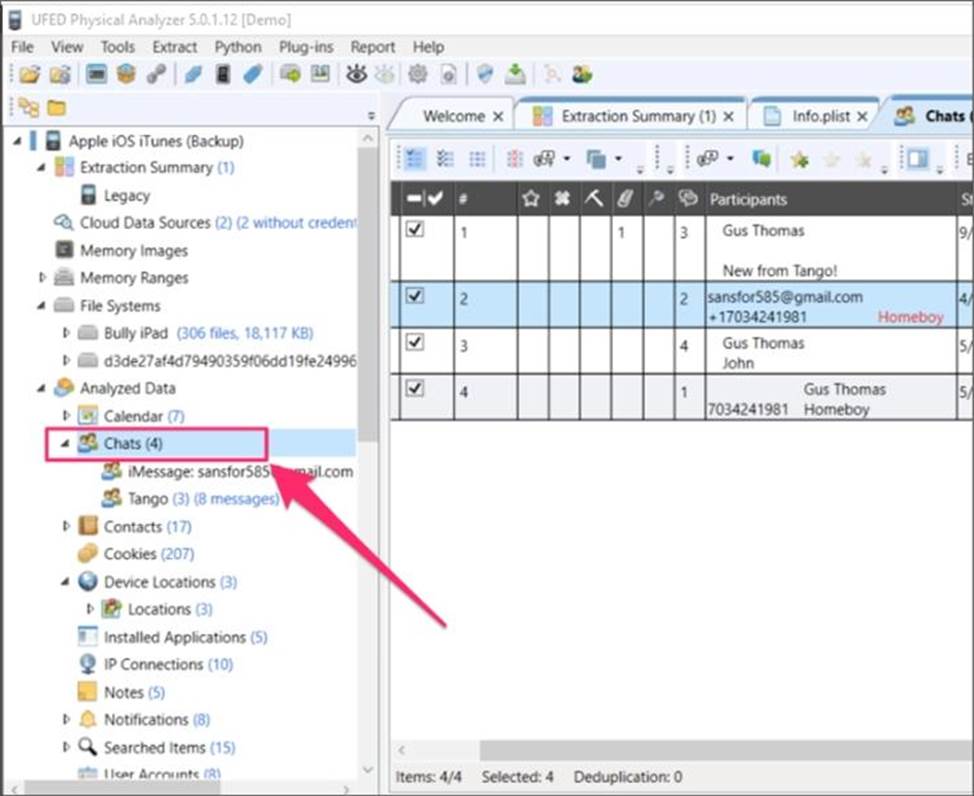
정답:
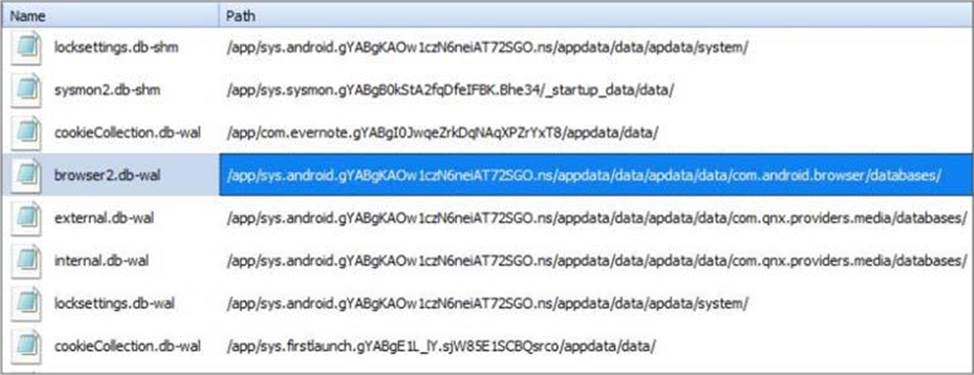
정답:
Explanation:
Reference: https://forums.crackberry.com/blackberry-q10-f272/protected-media-911023/
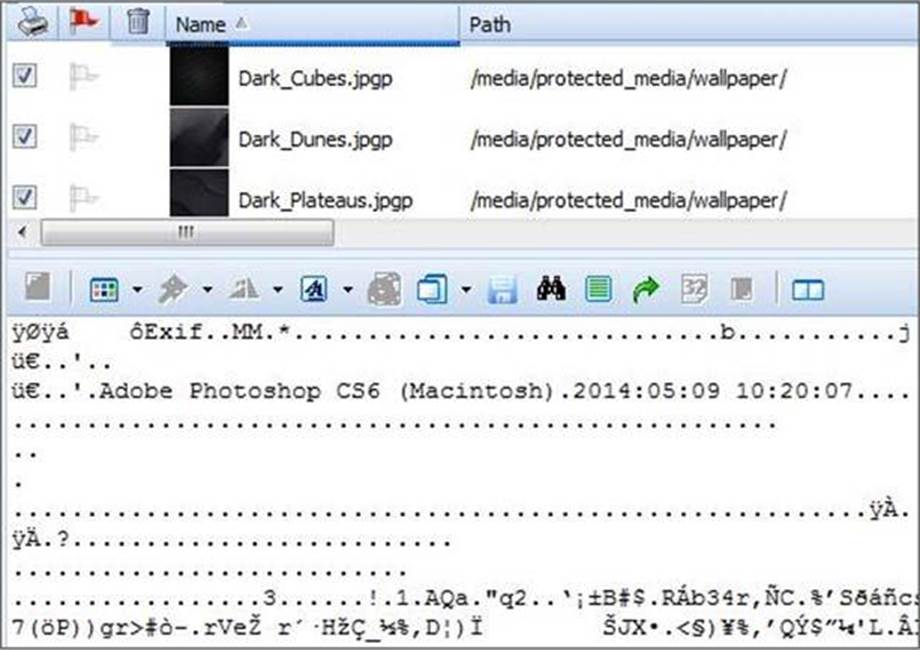
정답:
Explanation:
Physical Analyzer offers the Timeline feature to narrow down what happened on the smartphone during a specific time, type, party, etc. This is commonly used to narrow down time periods. Data that is manually carved will not be shown here. There is also an option to create a custom timeline specification.
정답:
Explanation:
Reference: https://www.ctsforensics.com/assets/news/35550_Web-update.pdf
정답:
Explanation:
Reference: http://money.cnn.com/2015/09/21/technology/apple-xcode-hack/index.html
정답:
정답:
Explanation:
Reference: https://security.stackexchange.com/questions/95186/what-is-the-precise-difference-between-asignature-based-vs-behavior-based-antiv
정답:
정답:
정답:
Explanation:
Analyzing both the Event Logs (which are accessible in Oxygen Forensic Suite) and/or the Installed Applications (which is a feature available in Cellebrite Physical Analyzer) may lead you to additional data. If applications of interest were located in the Event Logs, a Keyword Search across the media may reveal more data related to the application.
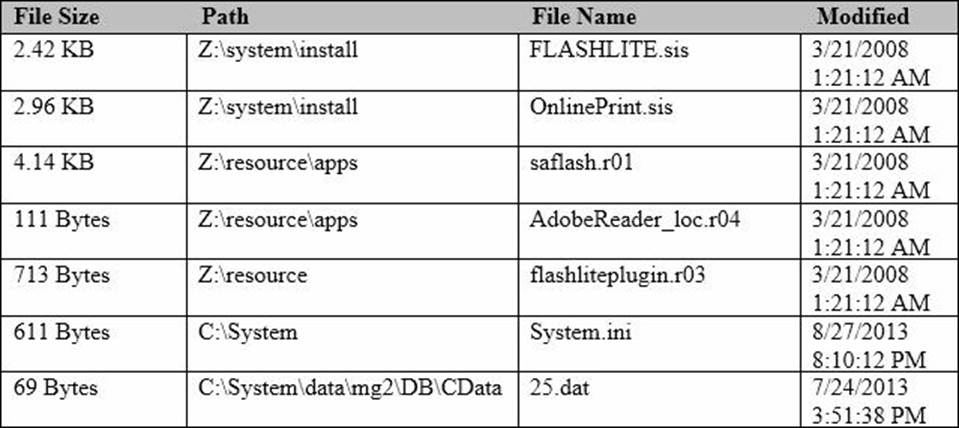
정답:
Explanation:
A sis.file is the package that Symbian uses to install applications on their OS compatible handsets. Knowing that you are investigating an application that is installed on the handset, first narrowing the files down to installer packages, or *.sis files, is a good starting point. Flash is an Adobe product making the most logical of the two remaining* .sis files for review, the FLASHLITE installer package. There are several other files related to “Flash” but as resource files, they provide supporting documentation and will not contain the .app file or code that was possibly malicious.