Question No : 1
when a role mapping policy should be used in an 802.1x service with Active Directory as the authentication source?
답을 확인하기
정답:
Question No : 2
Which Authorization Source supports device profile enforcement?
답을 확인하기
정답:
Question No : 3
Which most accurately describes the “Select All Matches” rule evaluation algorithm in Enforcement Policies?
답을 확인하기
정답:
Question No : 4
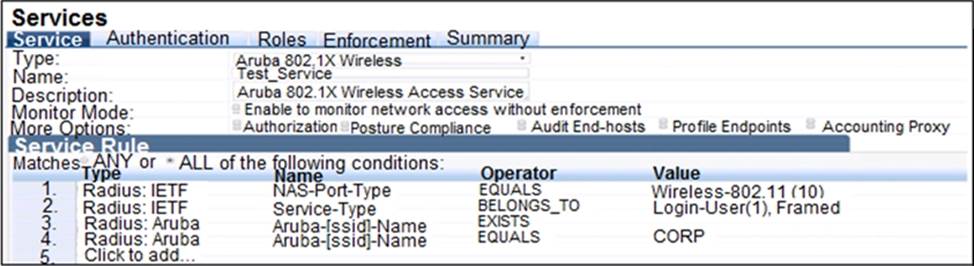
Refer to the exhibit.
Which user authentication request will match the service rules of the Policy Service shown?
답을 확인하기
정답:
Question No : 5
Which items would ClearPass be useful for? (Choose three.)
답을 확인하기
정답:
Question No : 6
Which actions are necessary to set up a ClearPass guest captive portal web login page to execute with no errors? (Choose three.)
답을 확인하기
정답:
Question No : 7
What is the function of the primary and backup servers when configuring an authentication source in ClearPass?
답을 확인하기
정답:
Question No : 8
Select three elements that are part of the authorization process. (Choose three.)
답을 확인하기
정답:
Question No : 9
Which statements describe subnet scans for static IP device discovery? (Choose two.)
답을 확인하기
정답:
Question No : 10
Your boss suggests that you configure a guest self-registration page in ClearPass for the Conference Events SSID.
Which advantages will this give? (Choose two.)
답을 확인하기
정답: