Salesforce Certified MuleSoft Developer II 온라인 연습
최종 업데이트 시간: 2025년03월23일
당신은 온라인 연습 문제를 통해 Salesforce MuleSoft Developer II 시험지식에 대해 자신이 어떻게 알고 있는지 파악한 후 시험 참가 신청 여부를 결정할 수 있다.
시험을 100% 합격하고 시험 준비 시간을 35% 절약하기를 바라며 MuleSoft Developer II 덤프 (최신 실제 시험 문제)를 사용 선택하여 현재 최신 60개의 시험 문제와 답을 포함하십시오.
정답:
Explanation:
To reuse Mule Maven plugin configuration across multiple individual Mule applications, the developer should use a parent pom.xml file. A parent pom.xml file defines common configuration for one or more child projects that inherit from it. The developer can specify common properties and dependencies for all child projects in the parent pom.xml file, such as Mule Maven plugin configuration, and then reference them in each child project’s pom.xml file using placeholders.
References:
https://docs.mulesoft.com/mule-runtime/4.3/mmp-concept#parent-pom
https://maven.apache.org/guides/introduction/introduction-to-the-pom.html#Project_Inheritance
정답:
Explanation:
The correct sequence of activities that takes place during the Maven build and deployment is validate, initialize, compile, test package, verify, install, deploy. These are Maven lifecycle phases that define a sequence of goals to execute during a build process. Each phase represents a stage in the build lifecycle and can have zero or more goals bound to it.
References: https://maven.apache.org/guides/introduction/introduction-to-the-lifecycle.html
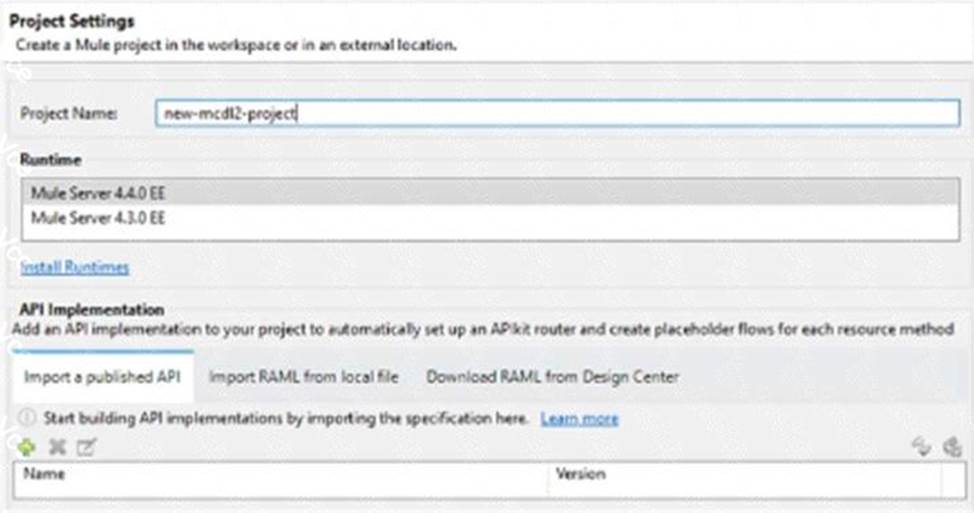
정답:
Explanation:
To create a new project that selects the correct API version and scaffolds the flows from the API specification, the developer should import a published API. This option allows importing an API specification that has been published to Anypoint Exchange or Design Center, and selecting a specific version of that API specification. The developer can also choose to scaffold flows based on that API specification.
References: https://docs.mulesoft.com/apikit/4.x/apikit-4-new-project-task
정답:
Explanation:
To enrich every log message with the order ID, the developer should use the Tracing module to set logging variables with a Mapped Diagnostic Context (MDC). The Tracing module allows adding custom key-value pairs to log messages using MDC variables. The developer can use Set Logging Variables operation to set the order ID as an MDC variable and then use it in any logger processor within the same thread or event.
References: https://docs.mulesoft.com/tracing-module/1.0/tracing-module-reference#set-logging-variables
정답:
Explanation:
When using XML SDK for creating custom message processors, all operations are public by default and can be used by any Mule application that imports them. There is no way to make an operation private or protected in XML SDK.
References: https://docs.mulesoft.com/mule-sdk/1.1/xml-sdk#operations
정답:
Explanation:
To validate the data before posting to the target system, the developer should add the JSON module dependency and add the validate-schema operation in the flow, configured to reference the schema. The JSON module provides a validate-schema operation that validates a JSON payload against a JSON schema and throws an error if the payload is invalid.
References: https://docs.mulesoft.com/json-module/1.1/json-validate-schema
정답:
Explanation:
To test that the payment API is working in production, the developer should create a health check endpoint that listens on a separate port and uses a separate HTTP Listener configuration from the API. This way, the developer can isolate the health check endpoint from the API traffic and avoid affecting the performance or availability of the API. The health check endpoint should return a simple response that indicates the status of the API, such as OK or ERROR.
References: https://docs.mulesoft.com/api-functional-monitoring/afm-create-monitor#create-a-monitor
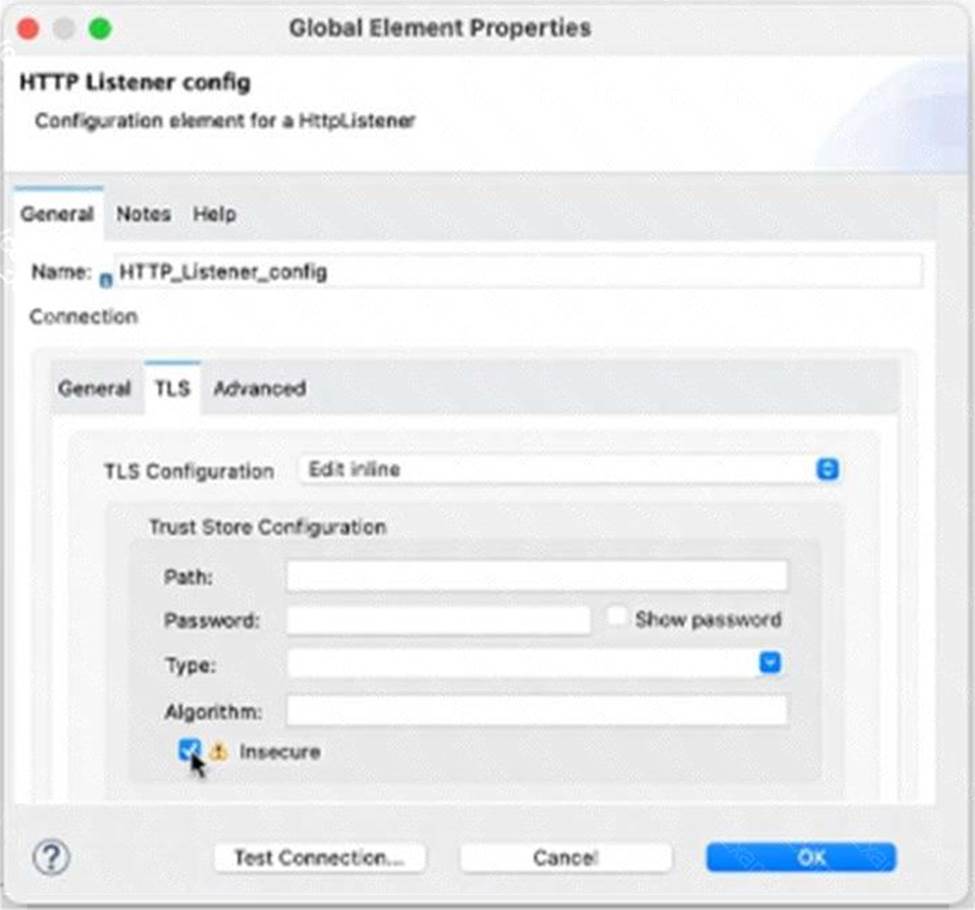
정답:
Explanation:
Based on the exhibit below, if ‘Insecure’ is selected as part of the HTTP Listener configuration, the HTTP
listener will only accept HTTP requests. This means that no TLS context will be configured for this listener
and no encryption or authentication will be applied to incoming requests. The protocol attribute of this listener will be set to HTTP instead of HTTPS.
References: https://docs.mulesoft.com/http-connector/1.6/http-listener-ref#insecure
정답:
Explanation:
To package a custom policy using the HTTP Policy Transform Extension, the developer needs to create an XML template file and a YAML configuration file. The XML template file defines the policy logic using Mule components and placeholders for user-defined properties. The YAML configuration file defines the metadata of the policy, such as its name, description, category, parameters, and dependencies.
References: https://docs.mulesoft.com/api-manager/2.x/http-policy-transform#packaging-the-policy
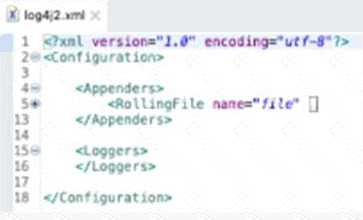
정답:
Explanation:
To log all the errors raised by the VM Connector, the developer needs to add an async logger with the name ‘org.mule.extension.vm’ and the level ‘ERROR’ inside the appenders tag of the log4j2.xml file. This will enable logging all error-level events generated by the VM Connector to the console appender.
References: https://docs.mulesoft.com/mule-runtime/4.3/logging-in-mule#configuring-custom-logging-settings
정답:
Explanation:
The Cache scope supports time to live (TTL) as a cache invalidation strategy without having to write any additional code. TTL specifies how long the cached response is valid before it expires and needs to be refreshed. The Cache scope also supports custom invalidation strategies using MEL or Data Weave expressions.
References: https://docs.mulesoft.com/mule-runtime/4.3/cache-scope#cache_invalidation
정답:
Explanation:
Mutual TLS (mTLS) is an extension of TLS that requires both parties (client and server) to present their certificates to each other during the handshake process. This way, both parties can verify each other’s identity and establish a secure connection. The authentication of the server happens before the authentication of the client, as the server sends its certificate first and then requests the client’s certificate.
References: https://docs.mulesoft.com/mule-runtime/4.3/tls-configuration#mutual-authentication
정답:
Explanation:
To enable mTLS authentication for HTTP Listener, the developer needs to set an appropriate keystore and truststore configuration for the listener. The keystore contains the certificate and private key of the Mule application that are used to prove its identity to clients. The truststore contains the certificates of trusted clients that are allowed to access the Mule application.
References: https://docs.mulesoft.com/mule-runtime/4.3/tls-configuration#mutual-authentication
정답:
Explanation:
secure::tiskeystore,keyPassowrdShor : ofCorrectAnswerOnly:Toreferenceasecurepropertyvaluewithin
In this case, the property name is tiskeystore,keyPassword, so the correct syntax is ${secure::tiskeystore,keyPassowrd}.
References: https://docs.mulesoft.com/mule-runtime/4.3/secure-configuration-properties#referencing-secure-properties
정답:
Explanation:
To manually approve or reject request access when registering a client application with an existing API
instance or API Group instance, it is required to configure the SLA tier for the application and have one of the following roles or permissions: Organization Administrator, API Manager Environment Administrator, or Manage Contracts permission. These roles or permissions allow managing client applications and contracts in API Manager.
References: https://docs.mulesoft.com/api-manager/2.x/client-applications#managing-client-applications-and-contracts