Microsoft Security Compliance and Identity Fundamentals 온라인 연습
최종 업데이트 시간: 2025년03월22일
당신은 온라인 연습 문제를 통해 Microsoft SC-900 시험지식에 대해 자신이 어떻게 알고 있는지 파악한 후 시험 참가 신청 여부를 결정할 수 있다.
시험을 100% 합격하고 시험 준비 시간을 35% 절약하기를 바라며 SC-900 덤프 (최신 실제 시험 문제)를 사용 선택하여 현재 최신 46개의 시험 문제와 답을 포함하십시오.
정답:
Explanation:
Information barriers are supported in Microsoft Teams, SharePoint Online, and OneDrive for Business. A compliance administrator or information barriers administrator can define policies to allow or prevent communications between groups of users in Microsoft Teams. Information barrier policies can be used for situations like these:
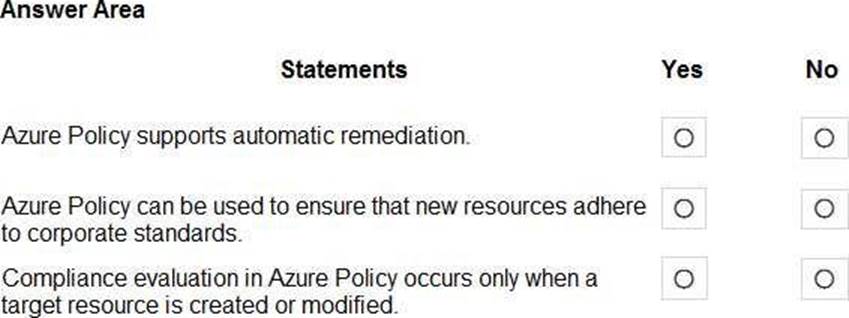
정답: 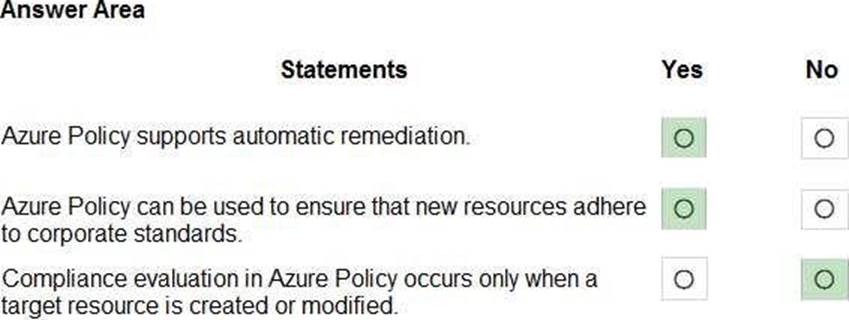
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/governance/policy/overview
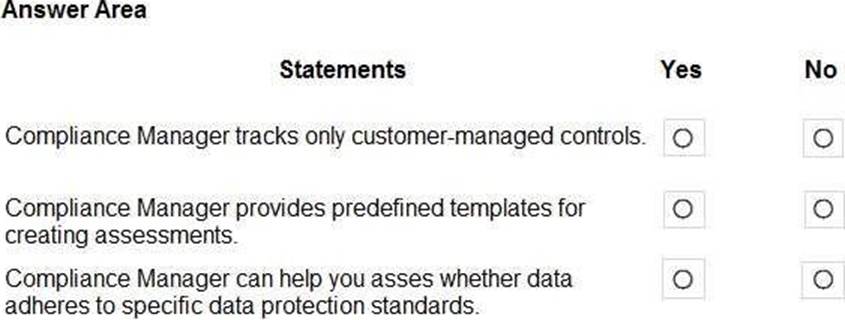
정답: 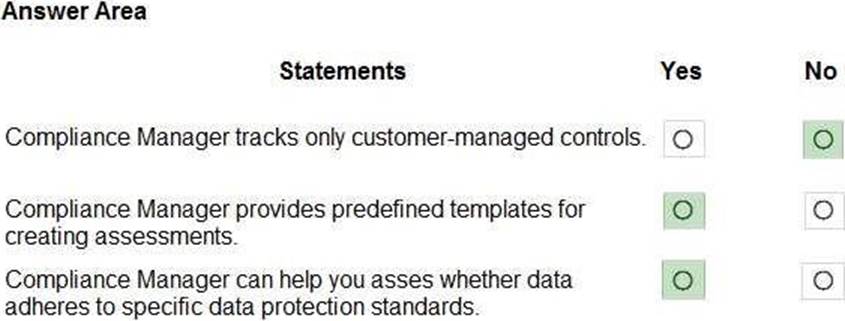
Explanation:
Box 1: No
Compliance Manager tracks Microsoft managed controls, customer-managed controls, and shared controls. Box 2: Yes
Box 3: Yes
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-manager?view=o365-worldwide
정답:
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/information-protection?view=o365-worldwide
정답: 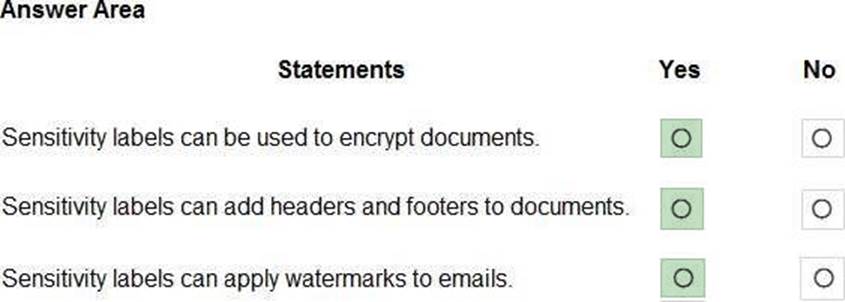
Explanation:
Box 1: Yes
You can use sensitivity labels to provide protection settings that include encryption of emails and documents to prevent unauthorized people from accessing this data.
Box 2: Yes
You can use sensitivity labels to mark the content when you use Office apps, by adding watermarks, headers, or footers to documents that have the label applied.
Box 3: NO
https://docs.microsoft.com/en-us/information-protection/deploy-use/configure-policy-markings

정답: 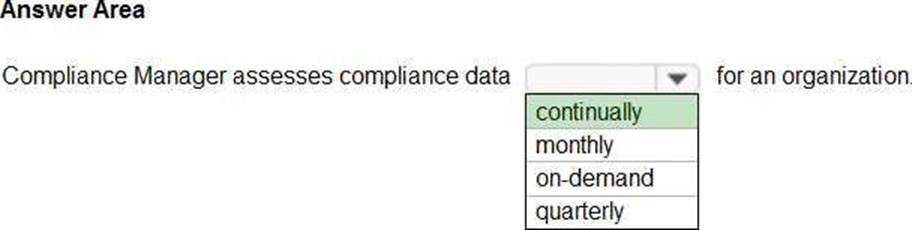
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-score-calculation?view=o365-worldwide#how-compliance-manager-continuously-assesses-controls
정답:
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/dlp-learn-about-dlp?view=o365-worldwide
정답:
Explanation:
The Content Search tool in the Security & Compliance Center can be used to quickly find email in Exchange mailboxes, documents in SharePoint sites and OneDrive locations, and instant messaging conversations in Skype for Business.
The first step is to starting using the Content Search tool to choose content locations to search and configure a keyword query to search for specific items.
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/search-for-content?view=o365-worldwide

정답: 
Explanation:
Box 1: No
Box 2: Yes
Leaked Credentials indicates that the user's valid credentials have been leaked.
Box 3: Yes
Multi-Factor Authentication can be required based on conditions, one of which is user risk.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection
https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/concept-identity-protection-risks
https://docs.microsoft.com/en-us/azure/active-directory/authentication/tutorial-risk-based-sspr-mfa
정답: 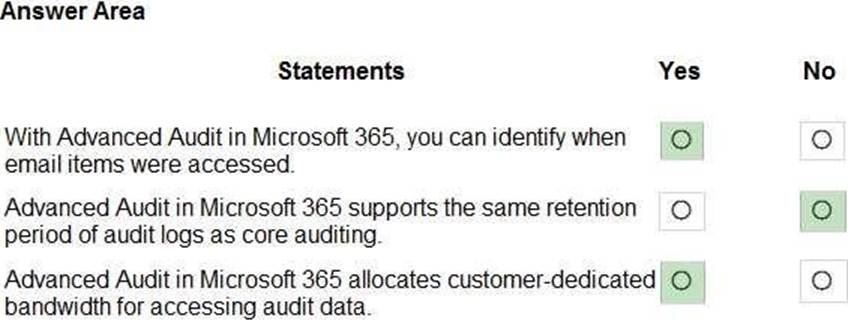
Explanation:
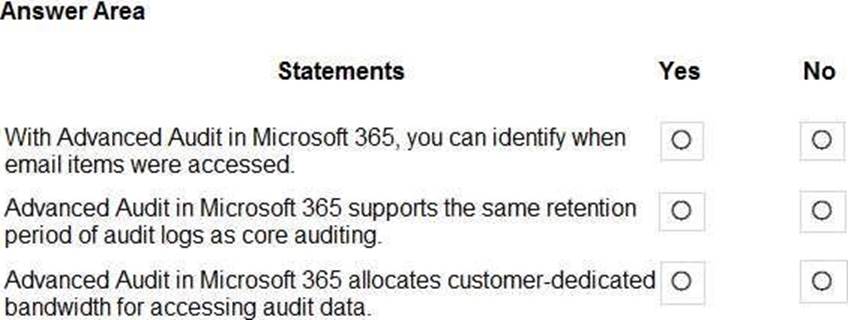
Box 1: Yes
The MailItemsAccessed event is a mailbox auditing action and is triggered when mail data is accessed by mail protocols and mail clients.
Box 2: No
Basic Audit retains audit records for 90 days.
Advanced Audit retains all Exchange, SharePoint, and Azure Active Directory audit records for one year. This is accomplished by a default audit log retention policy that retains any audit record that contains the value of Exchange, SharePoint, or AzureActiveDirectory for the Workload property (which indicates the service in which the activity occurred) for one year.
Box 3: yes
Advanced Audit in Microsoft 365 provides high-bandwidth access to the Office 365 Management Activity API.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/advanced-audit?view=o365-worldwide
https://docs.microsoft.com/en-us/microsoft-365/compliance/auditing-solutions-overview?view=o365-worldwide#licensing-requirements
https://docs.microsoft.com/en-us/office365/servicedescriptions/microsoft-365-service-descriptions/microsoft-365-tenantlevel-services-licensing-guidance/microsoft-365-security-compliance-licensing-guidance#advanced-audit
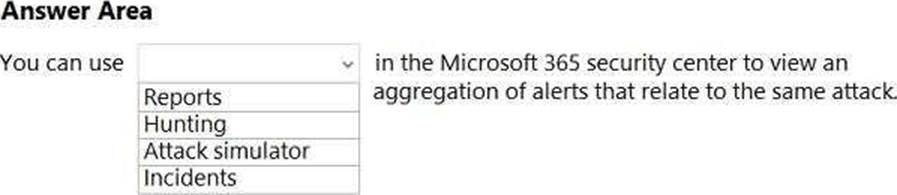
정답: 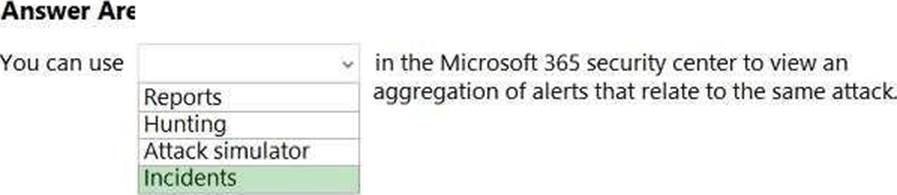
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/security/defender/threat-analytics?view=o365-worldwide

정답: 
Explanation:
Box 1: Yes
Azure Defender provides security alerts and advanced threat protection for virtual machines, SQL databases, containers, web applications, your network, your storage, and more
Box 2: Yes
Cloud security posture management (CSPM) is available for free to all Azure users.
Box 3: Yes
Azure Security Center is a unified infrastructure security management system that strengthens the security posture of your data centers, and provides advanced threat protection across your hybrid workloads in the cloud -whether they're in Azure or not -as well as on premises.
Reference:
https://docs.microsoft.com/en-us/azure/security-center/azure-defender
https://docs.microsoft.com/en-us/azure/security-center/defender-for-storage-introduction https://docs.microsoft.com/en-us/azure/security-center/security-center-introduction

정답: 
Explanation:
Microsoft Azure Sentinel is a scalable, cloud-native, security information event management (SIEM) and security orchestration automated response (SOAR) solution.
Reference: https://docs.microsoft.com/en-us/azure/sentinel/overview
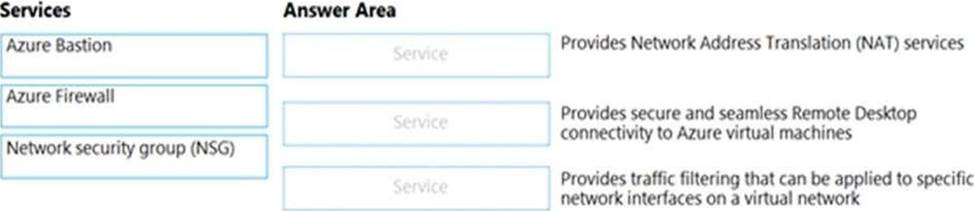
정답: 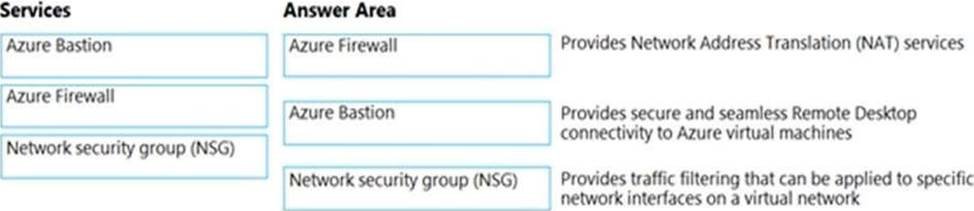
Explanation:
Box 1: Azure Firewall
Azure Firewall provide Source Network Address Translation and Destination Network Address Translation.
Box 2: Azure Bastion
Azure Bastion provides secure and seamless RDP/SSH connectivity to your virtual machines directly from the Azure portal over TLS.
Box 3: Network security group (NSG)
You can use an Azure network security group to filter network traffic to and from Azure resources in an Azure virtual network.
Reference:
https://docs.microsoft.com/en-us/azure/networking/fundamentals/networking-overview
https://docs.microsoft.com/en-us/azure/bastion/bastion-overview
https://docs.microsoft.com/en-us/azure/firewall/features
https://docs.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
정답:
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/microsoft-defender-endpoint? view=o365-worldwide